Reviewing Kansas’s Procedures for Election Security, Part 2
Introduction
Senator Dennis Pyle requested this audit, which the Legislative Post Audit Committee authorized at its April 22, 2022 meeting.
Objectives, Scope, & Methodology
The audit request included 5 questions. For reporting purposes, we divided them into 2 separate audit reports. Part 1 answered questions 3 – 5. This report, Part 2, answers questions 1 and 2, which we combined into the following question:
- Do county election offices have adequate policies and practices to ensure the accuracy and security of voting machines, ballots, storage units, and devices used to tabulate votes during elections?
We reviewed 15 counties’ policies and practices during the 2022 elections to answer the question. We identified national election security best practices and chose 50 individual best practices to review. We chose those best practices based on which ones we thought were most critical to accuracy and security. Then we determined whether state law and regulations included those practices.
We also reviewed whether 15 judgmentally selected counties had written policies for those practices. And we reviewed whether these 15 counties carried them out in practice during either the primary or general election in 2022. To do this, we reviewed available documentation, inspected counties’ election offices and storage facilities, and talked to county officials. We selected the 15 counties based on things like geographic location, number of voters, and the types of voting machines they used. Even though we only reviewed 15 of the 105 counties in Kansas, our selection included many of the largest counties. For example, the 15 counties we reviewed had a total population of 1.6 million in 2020, which is 56% of the 2.9 million total Kansas population at that time. Finally, we reviewed documentation from and talked to citizens concerned with election integrity.
More specific details about the scope of our work and the methods we used are included throughout the report as appropriate.
Important Disclosures
We conducted this performance audit in accordance with generally accepted government auditing standards. Those standards require that we plan and perform the audit to obtain sufficient, appropriate evidence to provide a reasonable basis for our findings and conclusions based on our audit objectives. Overall, we believe the evidence obtained provides a reasonable basis for our findings and conclusions based on those audit objectives.
Audit standards require us to report our work on internal controls relevant to our audit objectives. They also require us to report deficiencies we identified through this work. Most of our work for this audit consisted of reviewing counties’ controls for securing their elections. We found that each of the 15 counties we judgmentally selected for review had control design or practice deficiencies, as described in more detail later. Our audit results aren’t projectable to other counties. But the samples we reviewed are sufficient to reveal problems with the design or practice of counties’ security controls.
Our audit reports and podcasts are available on our website (www.kslpa.org).
The 15 counties we reviewed had some security practices that were adequate and others that were inadequate, but none had adequate written policies.
Background
Elections are complex and require lots of people and processes.
- Operating and overseeing an election requires many people and processes working at different times and locations. Figure 1 lists the major steps necessary to run an election. As the figure shows, dozens of things must happen before, during, and after election day for an election to run smoothly.
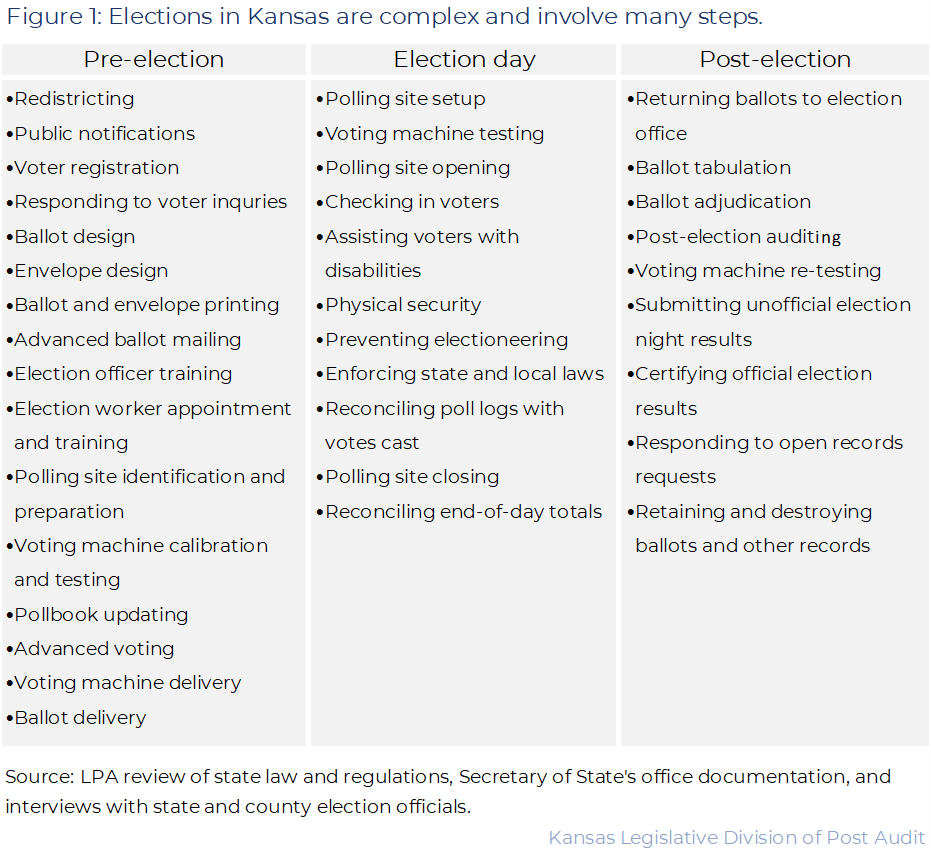
- The time constraints put on election processes makes this even more complicated. All these steps must take place within specific weeks, days, or hours. For example, state law (K.S.A. 25-106) says polling places can only be open on election day for a maximum of 14 hours.
- Successfully securing such complex processes requires robust policies and practices and effective training for the people who will carry them out. These policies and practices should exist for every phase of the election, including before and after the period polling places are open.
Each of Kansas’s 105 counties has a county election officer responsible for overseeing all elections in their county, including creating security policies.
- In 101 counties, the elected county clerk is the county election officer. They and their staff are responsible for administering county elections on top of their non-election duties, like county payroll and tax assessments. Many of these processes must occur at the same time as county clerks’ election preparations.
- State law (K.S.A. 19-3419) requires the Secretary of State to appoint separate, full-time election commissioners in counties with populations over 125,000. Johnson, Sedgwick, Shawnee, and Wyandotte counties have election commissioners. This commissioner serves as the county election officer. They don’t have non-election duties on top of this like county clerks do.
- County election officers oversee all aspects of elections in their counties. This includes establishing security policies and ensuring both full-time county staff and volunteer election workers correctly understand and carry them out.
County election officers appoint election workers who perform frontline election duties, including carrying out security policies.
- County election officers rely on county staff and volunteer county election workers to help run elections. County election workers help during many phases of elections, including before, on, and after election day. State law (K.S.A. 25-2808) generally requires each polling place to have 3 or more election workers. This includes a supervisor who’s responsible for overseeing the polling place and the other election workers. Part 1 of this report describes these workers in more detail.
- Election workers do the frontline work necessary to hold an election. They do things like open and close polling places, check voters in and assist them, and distribute and collect ballots. In many counties, they also transfer electronic election equipment, ballots, and other materials to and from polling places.
- To ensure election security, election workers should carry out all processes in accordance with the policies established by the county election officer. Election workers should understand why the policies are important and how to correctly practice them.
Election processes vary across counties.
- State law gives county election officers discretion over how to run elections in their counties. Differences are largely related to the number of voters in the county, since it’s more complicated to accommodate more voters. Each county has a county election office, but these offices look and function very differently.
- Larger counties need more full-time county staff, volunteer election workers, electronic equipment, and polling places. For instance, one large county we reviewed has about 2,000 pieces of equipment and 150 polling places. Contracted moving companies and dozens of election workers need over a week to set up for election day. By contrast, one small county we reviewed has 5 pieces of equipment and 1 polling place. The county clerk and her deputy simply drive the equipment to the polling place in their personal vehicles the night before the election.
- Larger counties need larger offices and storage facilities to manage their staff, election workers, and equipment. The election office in one large county we reviewed has a large standalone office and on-site warehouse facility with robust security. By contrast, one small county clerk’s office we reviewed has an open, 2-person office space in the county’s historic courthouse building and a small, lockable storage room in the publicly accessible basement.
Modern elections rely heavily on electronic voting and tabulation machines and election management computers.
- All Kansas counties except 1 use electronic equipment to administer elections. This is the primary way votes are cast and counted. Electronic equipment affects every stage of the election process.
- Polling places have voting machines called ballot marking devices. Voters can use these machines to make their selections on a touchscreen or through an accessibility device. The machine then prints a completed ballot reflecting the voter’s choices. But voters can also hand-complete paper ballots rather than use these machines. In some counties, this may be more common than voting with a ballot marking device.
- Voters insert their hand- or machine-completed ballots through a separate tabulation machine called an optical scanner. These scanners read and count the ballots and store the results on election results storage media, such as a USB stick. Mail-in ballots are also scanned by tabulation machines, but at the election office rather than the polling places.
- The election results storage media is hand carried to the county election office and plugged into the county’s election management computer. This computer aggregates all the polling places’ results and determines each race’s countywide winners. State law (K.S.A. 25-4403) doesn’t allow these computers to be connected to the Internet, and best practices say they shouldn’t have any non-election software on them.
- Sheridan County is the only Kansas county that hand-counts paper ballots and doesn’t use any electronic equipment. They make a voting machine available at each polling place to comply with federal Americans with Disabilities Act requirements.
- The official county canvass to determine the results is completed after these processes. It starts the Monday after the election at the earliest. It includes confirming staff research on the validity of any provisional ballots. Voters receive provisional ballots whenever there’s a question about their eligibility to vote, such as an address or name change. The county board of canvassers reports the county’s vote totals to the state board of canvassers, which includes it in the statewide canvass to determine the statewide election results.
Election Security Best Practices
We identified and reviewed election security best practices from the federal election agency.
- To understand what security-related policies and practices county election offices should have, we reviewed best practices from the U.S. Election Assistance Commission (EAC).
- The EAC is a federal agency that tests and certifies voting machines nationwide and publishes voluntary voting system guidelines. States and counties aren’t required to follow these guidelines. But the guidelines provide best practices states and counties can reference and use as appropriate. We talk more about these guidelines in Appendix C.
- EAC best practices cover more areas than we had time or resources to review. We selected 50 practices we thought were likely to be important for most counties’ security. They also covered the security areas EAC officials told us were most important for securing elections.
The best practices we reviewed fall into 5 general election security and integrity categories.
- Election security policies and practices should address potential risks in every part of the election process. We organized the 50 best practices we identified into 5 high-level categories, each of which includes several practices. Appendix B lists the individual practices that fall under each category.
- (1) Overall process security refers to basic practices that set the stage for a secure election. This includes things like buying certified electronic equipment, inventorying it, and tracking anything that happens with it. These practices help ensure equipment meets national standards and will accurately record and tabulate votes.
- (2) Election management computer security refers to securing this computer so it’ll accurately aggregate countywide results. This includes things like physically securing it from unauthorized access, logging all computer activity, and keeping it disconnected from the Internet. These practices help prevent intentional or accidental compromises that might affect the election results.
- (3) Ballot security refers to tracking ballot activity. This includes things like noting how many ballots are sent from the county election office to the polling places, comprehensively tracking how they’re used, and using controls to ensure all legal ballots are tallied. These practices help exclude any invalid ballots someone might try to add either at the polling place or during transfer.
- (4) Voting and tabulation machine security refers to securing these machines so they’ll accurately reflect voters’ choices on election day. This includes things like testing them when they’re first purchased, physically securing them while they’re stored between elections, and testing them again before they’re used. These practices help prevent intentional or accidental compromises that might cause things like votes being counted for the wrong candidates.
- (5) Transfer and movement security refers to securing electronic equipment, election results media, and ballots during transfer from the county election office to the polling place and back. This includes hand carrying election results, tracking equipment and election results movement, and sealing equipment and election results during transfer. These practices help prevent intentional or accidental equipment compromises and tampering with ballots or election results media during transfer.
- Appendix C outlines some common election security concerns we heard from concerned citizens. Some of these best practices may help address them.
Kansas has only a few high-level election security-related laws and regulations related to these 5 best practice categories.
- We reviewed state law and regulations to determine whether they reflected the national best practices we identified.
- State law and regulations included very few best practices. Overall, law and regulations fully reflected 8 and partially reflected 3 of the 50 best practices we focused on. State law and regulations were more general than the best practices. For example, state law (K.S.A. 25-4406 and 25-4613) requires voting and tabulation machines to be EAC certified. But best practices specify that these machines’ software should come from a trusted source, and any vendor modifications or updates should also be EAC approved.
- State law included 5 additional election security requirements our selected best practices didn’t. Several related to conducting public post-election accuracy tests on all tabulation machines (K.S.A. 25-4610). We added these requirements to our review, for a total of 55 election security controls we evaluated counties on.
- State law and regulations’ more general, less detailed requirements give counties more flexibility in how they secure their elections. More specific state law and regulations equally applicable to all counties may burden smaller counties that don’t have the same security needs or resources as larger counties.
County Evaluation Methodology
We reviewed whether 13 counties had policies and practices that aligned with 55 best practices and state laws during the 2022 primary or general elections.
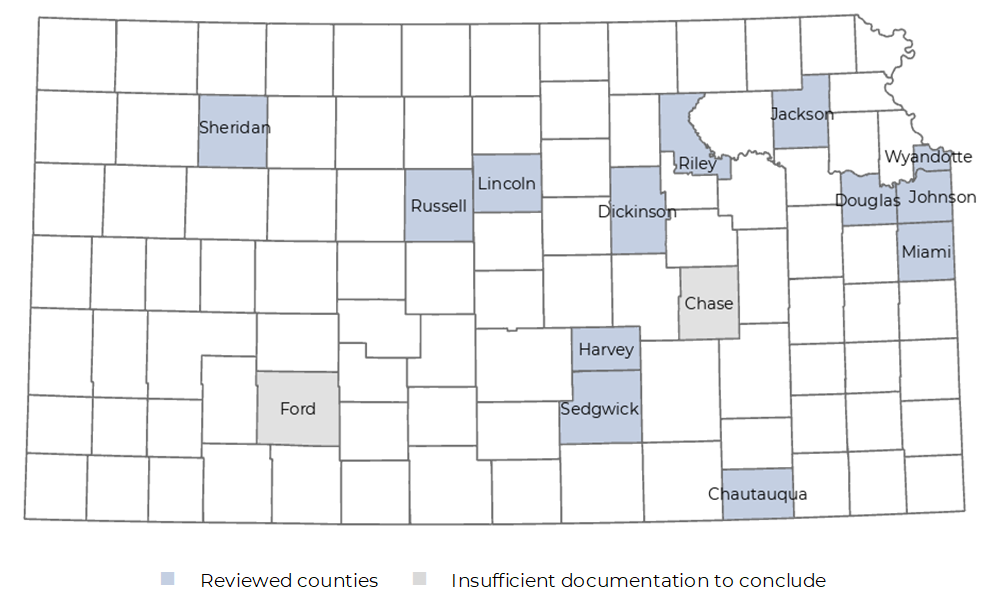
- We reviewed 13 counties’ policies and practices against the best practices and state laws we identified. These counties included Chautauqua, Dickinson, Douglas, Harvey, Jackson, Johnson, Lincoln, Miami, Riley, Russell, Sedgwick, Sheridan, and Wyandotte. We chose them because they varied in things like geographic location, number of voters, and the types of voting machines they used. We didn’t consider these counties’ 2020 election results when making our selection. Appendix D outlines these counties in greater detail.
- To review these counties, we talked extensively to county officials and spent time on site inspecting their election offices and storage facilities. We observed some security practices through these visits. We also reviewed their written security policies, as well as available documentation to verify what the counties did in practice in 2022. For some counties we ended up reviewing a few dozen pages of documentation, and for others we reviewed hundreds of pages of documentation to reach our conclusions.
- We based some conclusions on non-projectable samples of voting and tabulation machines or polling places because we didn’t have the time or resources to review all machines and polling places in each county. The samples we reviewed are sufficient to reveal problems with the design or execution of counties’ security controls. But because we didn’t review all machines or polling places, additional control weaknesses could potentially exist.
- We randomly selected a sample of equipment and polling places to review in each county. The size of our samples varied based on county size. For instance, we reviewed documentation for 15 to 20 polling places and 15 to 20 machines in Johnson County. By contrast, we reviewed documentation for both of Lincoln County’s 2 polling places and a sample of 5 machines.
We reviewed Chase County and Ford County’s policies but couldn’t verify their practices because they sealed most of their 2022 election documentation.
- We intended to review 15 counties. In addition to the 13 counties listed above, we also selected Chase County and Ford County for review. For each county, we intended to review their written security policies, as well as available documentation to verify what the counties did in practice in 2022. Toward the beginning of our work, we asked all the counties to not discard or seal the election-related documentation we wanted to review.
- We reviewed these 2 counties’ security-related policies. But unlike the other 13 counties we looked at, they sealed most of the documentation showing the practices they followed in 2022. They told us they sealed these documents in the same containers as their ballots. We couldn’t review them because state law (K.S.A. 25-2708 and 25-3107) requires sealed ballots to remain sealed. We reviewed what these counties left unsealed as well as some practices while visiting in person, but this wasn’t enough to draw conclusions.
- Secretary of State’s office officials told us county officials often indiscriminately seal election documents with ballots. But this doesn’t align with the purpose of ballot sealing, which is to maintain an accurate paper record of the election results. Further, it doesn’t align with state law. The Kansas Open Records Act (K.S.A. 45-216) requires public records to remain open for inspection unless state law provides an exception. Election documentation we reviewed in other counties included things like ballot activity or equipment transfer records. State law doesn’t provide an exception for election-related records like these.
- Further, Ford County officials didn’t let us inspect their election management computer. We did this in the other 14 counties, including Chase County. As such, we don’t know whether Ford County’s computer was disconnected from the Internet or had any non-election software on it.
There are important caveats to note about the work we did.
- We were asked whether county election offices have adequate policies and practices to ensure the accuracy and security of voting machines, ballots, storage units, and devices used to tabulate votes during elections. In other words, whether Kansas counties have the right election security tools in place.
- Because Kansas elections are decentralized across 105 counties, we chose a selection of counties to get a sense of whether they had good policies and practices in those specific areas.
- Our conclusions are based on either the documents counties provided or our own observations. In some cases, county election officials told us they had controls in place during the 2022 elections that aligned with best practices but couldn’t provide documents or show us during our visit. Some counties may have indeed followed best practices in 2022 but weren’t counted as doing so because we couldn’t verify this. We don’t know how common this might have been.
- We didn’t evaluate whether counties’ security controls worked as intended or otherwise how they might have affected the 2022 elections. For example, we reviewed whether counties kept lists of the people who were given keys to secure storage facilities. But we didn’t determine whether these lists were limited to only the appropriate staff. As such, we can conclude on whether the counties have controls to track who has access but not whether they’re appropriately limiting this access.
- We didn’t evaluate whether the 2022 elections in the counties we reviewed were correctly tabulated or accurately reflected the will of the voters in those counties. Such determinations were outside the approved audit scope.
- Our audit scope focused on the 2022 elections. We talked to county officials about what 2020 election documentation might also be available. But we couldn’t review 2020 documentation because county election officials had sealed or destroyed it by the time we began our audit work, in alignment with state and federal law.
- We didn’t review all important aspects of elections. The EAC has numerous best practices, covering all aspects of elections. We focused on 55 specific best practices and state laws related to security of voting machines, ballots, storage units, and devices used to tabulate votes. The scope of this audit did not have us review controls relating to voter registration, mail-in voting, ballot drop boxes, or the post-election auditing process. Practices in these areas would complement and back up the practices discussed in this report.
County Evaluation Results
The 13 counties we reviewed generally had adequate overall process security practices.
- The best practices in this category are basic practices that set the stage for a secure election. Figure 2 shows a summary of the results for the overall process security practices we reviewed, like ensuring counties bought certified equipment and had processes for inventorying it.
- This overall process security area has 10 best practices we reviewed. For example, the inventory practice includes 5 components, including that the inventory is: (1) updated, (2) includes quantities, (3) includes permanent and unique serial numbers, (4) tracks when equipment is checked in and out, and (5) tracks repairs. For reporting purposes, we rolled the 10 best practices we reviewed into 3 areas. Appendix B shows these details for every best practice area included here.
- As the figure also shows, there are 4 possible shades of blue. The darkest shade of blue indicates the best practices are mostly or totally present (75%-100%), and the lightest shade of blue indicates the best practices are mostly or totally absent (0%-25%). Overall, we thought a county was adequate if its practices fell into the 2 darkest shades of blue. This doesn’t necessarily mean they had no issues, simply that they had at least half the practices we looked for in each area.
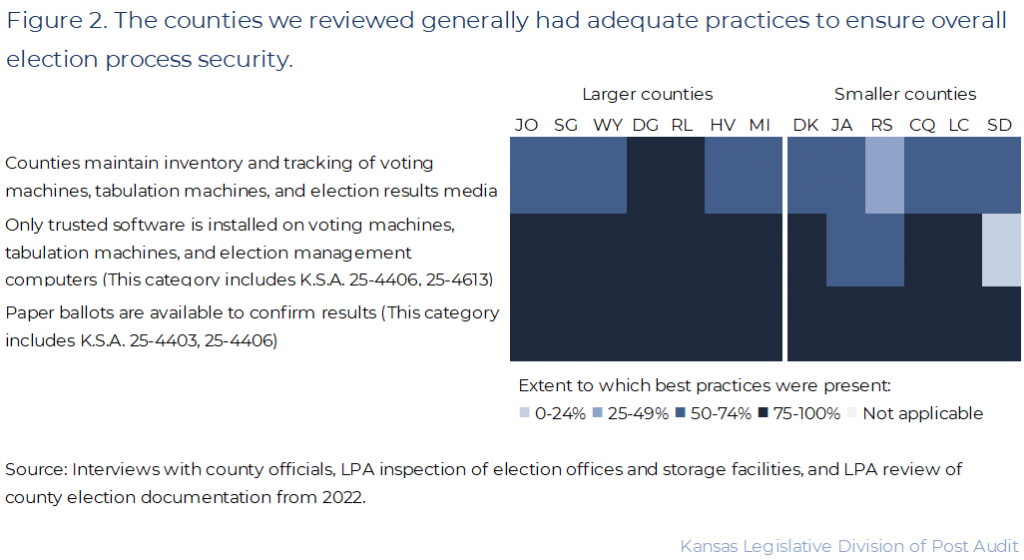
- As Figure 2 shows, the counties we reviewed generally had strong practices for ensuring only trusted software was installed on machines and that paper ballots were used. Overall, counties’ inventorying practices weren’t quite as strong, though they were generally still adequate.
- For example, Douglas County and Riley County kept comprehensive inventories of their electronic equipment and election results media. These inventories included unique identifiers for each item and logs showing when and how each item had been repaired. Douglas County also used a scanning system to automatically log each time an item left from or returned to the county’s storage facility.
- Russell County kept an updated inventory of its equipment that included unique identifiers for each item. But it didn’t track repair information or log when equipment left from or returned to storage. Russell County also didn’t inventory its election results media. Not having an inventory of election results media was a common issue across the counties we reviewed.
With only a few exceptions, the 13 counties we reviewed also generally had adequate election management computer security practices.
- The best practices in this category help ensure the election management computer is secure and will accurately aggregate countywide results. Figure 3 shows a summary of results for election management computer security practices we reviewed, like ensuring counties physically secure their election management computer and monitor all activity on it.
- This security area has 11 best practices we reviewed for each county. For reporting purposes, we’ve compiled the results for each county into 3 main areas. All the best practices we reviewed are listed in Appendix B.
- As the figure shows, all counties demonstrated strong practices for ensuring their election management computers can’t be used for other purposes. Most of them also had strong practices for ensuring activity on those computers is monitored and that they’re secured from unauthorized access.
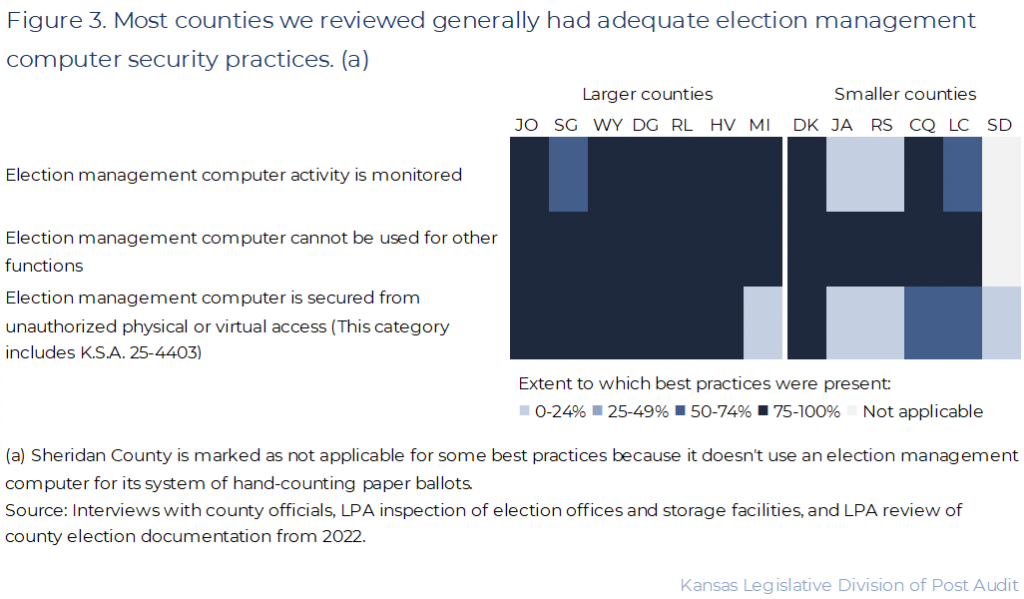
- For instance, counties like Douglas, Johnson, and Wyandotte had advanced election management computer security. Their computers were in locked, video-monitored rooms requiring keycode or badge access. These rooms had to be entered in pairs, and some logged each entry. The computers required complex passwords and logged all system activity. Finally, users’ access levels were limited to what they needed to do their jobs.
- Common control weaknesses in this category related to counties’ practices for physically securing their computers. These issues often came from counties’ space and resource limitations. Many smaller and medium-sized counties had to make do with existing space in their county courthouses instead of secured rooms devoted to their election management computers.
- For example, counties like Chautauqua and Lincoln used laptops rather than more permanent desktops or servers for their election management computers. We observed the laptops were locked away while not in use, but we couldn’t confirm that they were kept secure while in use. That’s because county officials used their laptops in the publicly observable and accessible county clerk’s office or county commission room on election day. But these small counties did well on things like monitoring computer access, logging computer activity, and requiring complex passwords.
- Some medium-sized counties, like Jackson and Miami, used desktops rather than laptops. They installed them in publicly observable and accessible spaces also used for other purposes, like conference rooms. But these counties didn’t have some practices smaller counties had in place, like monitoring computer access and requiring complex passwords.
- None of the election management computers we inspected could connect to the Internet or had non-election software on them.
County results varied, but ballot security practices were weaker overall than overall process or election management security.
- The best practices in this category track ballot activity and help ensure invalid ballots aren’t counted. Figure 4 shows a summary of results for the ballot security practices we reviewed, like ensuring counties have comprehensive processes for accounting for what happens to every ballot sent out from the election office.
- This security area has 7 best practices we reviewed for each county. For reporting purposes, we’ve compiled the results for each county into 2 main areas. All the best practices we reviewed are listed in Appendix B.
- As the figure shows, many counties had most of the ballot security practices we reviewed. However, they were generally weaker than counties’ overall process or election management security practices. Specifically, about half of the counties we reviewed had weak controls for accounting for all ballots and ensuring the correct number was tabulated.
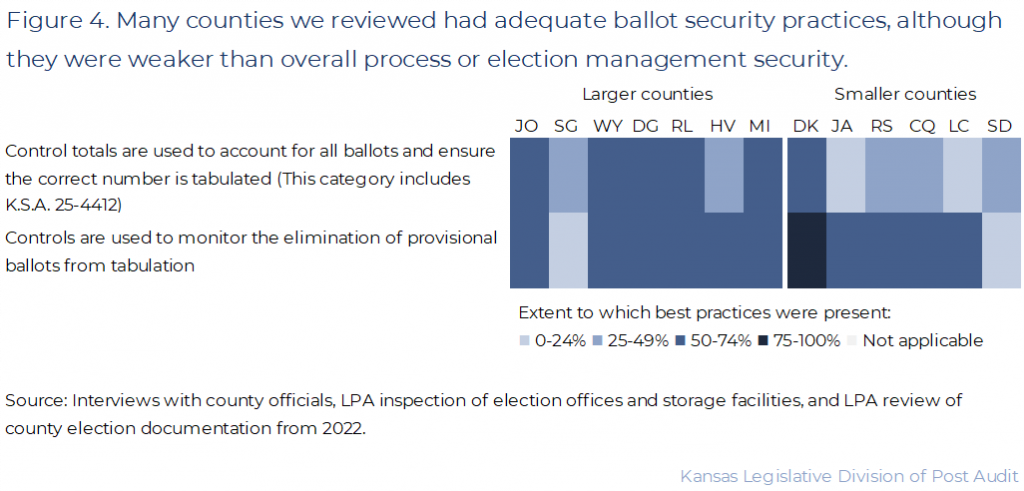
- For instance, Dickinson County had a good process to document how many ballots were sent to each polling place. This included tracking how many ballots were voted, voted provisionally, spoiled, or unused. They also documented how many voters used voting machines. Many counties missed this latter step, which is essential for accurate ballot accounting because it helps show how many paper ballots should’ve been used.
- Counties sometimes created standardized forms that could lead to robust ballot security practices if used properly. But many forms we reviewed weren’t filled out completely or correctly, undermining their value.
- For example, Sedgwick County created a form requiring polling places to balance the numbers of checked-in voters and used ballots each hour. Doing this periodically throughout the day would catch any extra ballots added to the total before too much time has passed. But of the 20 polling places we reviewed, we didn’t receive 6 forms from county officials, and 8 forms had problems. Many hours’ entries were partially or totally skipped, filled out inconsistently, or didn’t add up correctly. Imbalances weren’t explained.
- Jackson County had a form that could have captured ballot and voting machine information similar to Dickinson County’s form. But none of the 10 forms we reviewed were filled out correctly. Each was missing information needed to account for ballot activity. For instance, only 2 forms captured how many voters used voting machines, and 2 others were almost totally blank.
Most of the 13 counties we reviewed had inadequate voting and tabulation machine security practices except for physical security practices.
- The best practices in this category help ensure voting and tabulation machines are secure and accurately reflect voters’ choices on election day. Figure 5 shows summary results for the voting and tabulation machine security practices we reviewed, like ensuring counties physically secure their voting and tabulation machines and test them before they’re used in elections.
- This security area has 11 best practices we reviewed for each county. For reporting purposes, we’ve compiled the results for each county into 4 main areas. All the best practices we reviewed are listed in Appendix B.
- As the figure shows, most counties had adequate practices for physically securing their electronic equipment while in storage. But counties had weak practices for testing this equipment at the time of purchase or before or after elections.
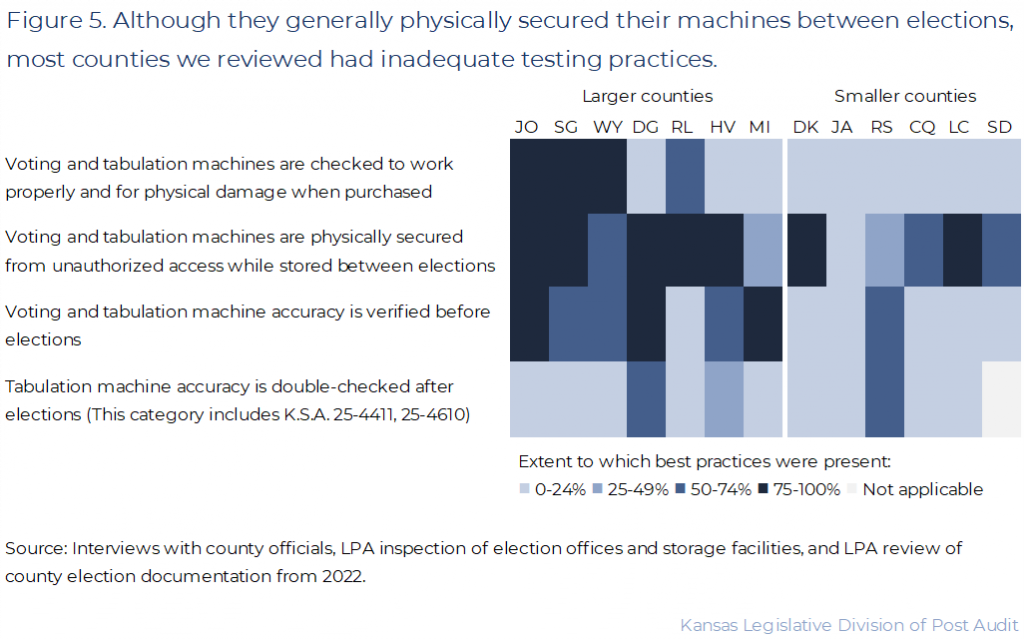
- For example, counties like Douglas, Harvey, Johnson, Riley, and Sedgwick stored voting and tabulation machines in locked, video monitored rooms. These counties required staff to scan their badges to enter except for Harvey County, which used a fingerprint scanner instead. These systems logged each time someone entered the storage room.
- But many counties didn’t provide documentation showing all their electronic equipment had undergone acceptance testing when the equipment was purchased. These tests ensure counties are receiving intact and correctly functioning machines when they first buy them. Officials from Chautauqua, Dickinson, Douglas, Harvey, and Lincoln counties said they or their vendor had done this testing but didn’t have documents showing this.
- We also found problems with most counties’ logic and accuracy testing practices before elections are held. These tests are critical because they verify that voting and tabulation machines will accurately record and count votes on election day.
- Chautauqua, Dickinson, Jackson, Lincoln, Riley, and Sheridan counties didn’t provide documentation showing they conducted logic and accuracy testing on all the machines we sampled. Some said they did this testing but didn’t document it, so we couldn’t verify this.
- Harvey, Russell, Sedgwick, and Wyandotte counties provided documents showing they tested the machines we sampled. But only 1 person did the tests. 2 people should perform logic and accuracy testing to ensure it’s done correctly and impartially.
- The counties we reviewed generally performed poorly on state law’s (K.S.A. 25-4411 and 25-4610) 2022 requirement that counties conduct public post-election tests on all their tabulation machines. This testing double-checks that all tabulation machines worked as expected during the election. Most counties did post-election tests, but the tests didn’t include all machines or all candidates and measures, as required by law. This could be because the law was new in 2022 and counties hadn’t yet had time to create processes for it.
Finally, the 13 counties we reviewed had some transfer and movement security practices that were adequate, but others that were generally inadequate.
- The best practices in this category help ensure electronic equipment, election results media, and ballots are secure when transferred from the county election office to the polling place and back. Figure 6 shows summary results for the transfer and movement security practices we reviewed, like ensuring counties track the movement of their election equipment and keep it sealed during transfer.
- This security area has 16 best practices we reviewed for each county. For reporting purposes, we’ve compiled the results for each county into 5 main areas. All the best practices we reviewed are listed in Appendix B.
- As the figure shows, most counties had stronger practices for monitoring equipment deployment to polling places and ensuring that election results were secured during transfer back to the election office. But they had inadequate practices for monitoring that equipment was secure at the polling places and safely returned after the election. This frequently reflected poor chain-of-custody documentation practices.
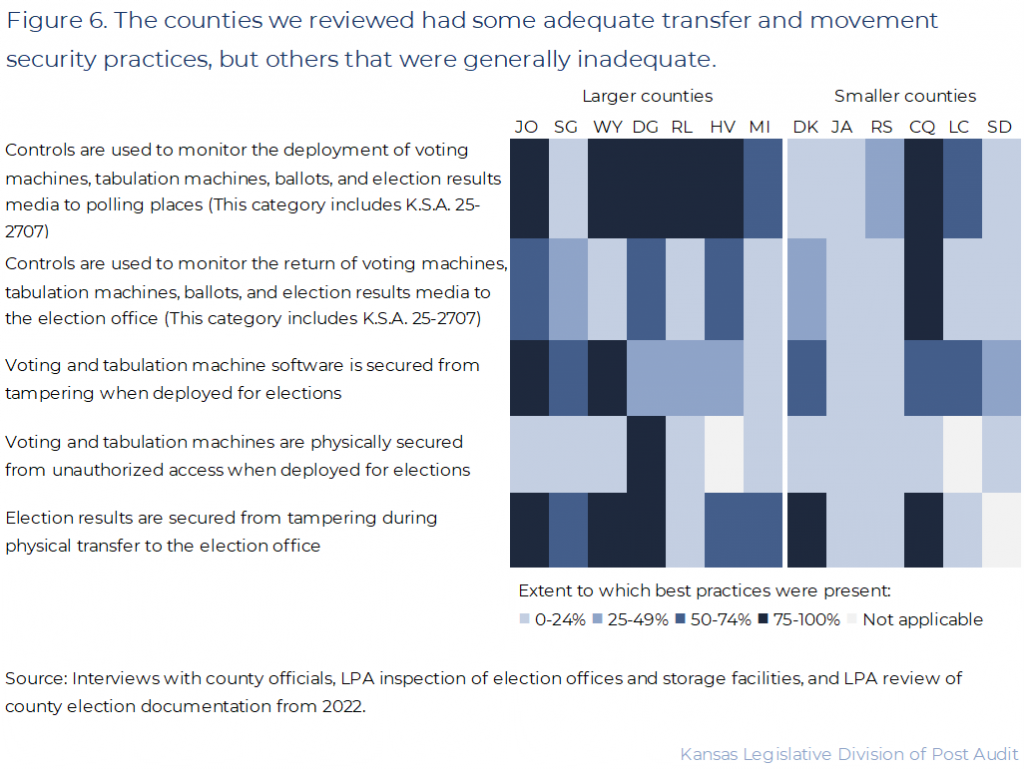
- For example, Johnson County tracked when and by whom all electronic equipment, paper ballots, election results media, and other supplies were transferred. These forms captured transfer out to and back from the polling places. Johnson County also applied tamper proof seals to voting and tabulation machines and to the pouches they used to transfer ballots and election results storage media back from polling places. Finally, they documented whether these seals were still intact upon arrival, to show they hadn’t been tampered with during transfer.
- Some counties created standardized forms they said recorded the transfer or arrival of things like election results media both to and from the central election office. But it wasn’t always clear what the documents were supposed to show, so we couldn’t verify this. For instance, Jackson, Lincoln, Miami, and Russell counties provided chain-of-custody documents that had signatures but didn’t say they were confirming the arrival of election results storage media to the election office. Such forms would make it easier for someone to sign while overlooking something they’re signing for, lessening its effectiveness as a control.
- In addition, only 1 person or 2 people from the same party carried completed ballots back from nearly all polling places in all counties that documented this. Many counties mitigated this by sealing the ballots during transfer. But this practice doesn’t comply with state law (K.S.A. 25-4611), which requires that bipartisan teams carry ballots back to the election office. County election officers told us they can’t get enough election workers of one party or the other to ensure they have bipartisan teams available when needed.
Larger counties generally had stronger security practices than smaller counties likely because of their greater security needs and resources.
- As Figures 2-6 show, larger counties generally followed more of the best practices we reviewed than smaller counties did. In those figures, we show results of 5 security areas and 17 summarized best practice control areas.
- For example, all 7 of the large counties we reviewed had adequate overall process security practices shown in Figure 2. But 2 small counties did not have adequate practices. That same pattern generally holds true for all 5 categories of practices we reviewed.
- On a county-by-county basis, all 7 of the large counties we reviewed had adequate security practices in 10 or more of the areas we reviewed. For example, Douglas and Johnson counties had the strongest practices. Their practices were adequate in 15 of 17 (88%) best practice areas we reviewed.
- Conversely, only 3 of the small counties we reviewed had adequate security practices in 10 or more of the areas we reviewed. These included Chautauqua (12 of 17, or 71%), Dickinson (11 of 17, or 65%), and Lincoln counties (10 of 16, or 63%). But Jackson and Sheridan counties had the weakest security practices. For example, Jackson County’s practices were adequate in only 5 of 17 areas (29%).
- Larger counties generally have stronger security practices than smaller counties because their elections require coordinating and overseeing more people and equipment. The sheer volume and complexity require larger counties to have more controls and better documentation to ensure things aren’t missed.
- Larger counties also have more financial and staff resources to dedicate to elections. For example, small counties like Chase, Lincoln, and Sheridan had only 1 full-time staff member in addition to the county clerk, who must also work on the other areas under the clerk’s responsibility. Larger counties have many more staff, and in counties with election commissioners they’re all dedicated to elections. Larger counties can also more easily afford certain practices, like installing video cameras.
No county in our sample had adequate practices for all the best practices and statutes we reviewed, but that doesn’t necessarily mean the elections aren’t secure.
- The federal EAC lays out an ideal system of security practices. Many practices complement or provide redundancy for one another. This means that if 1 practice is missing, others may be in place to secure the same area. If there was a bad actor at any stage in the process, the number of controls and their redundancy should minimize any adverse impact.
- The practices we reviewed are important components for securing elections, but we didn’t review all election controls. For example, we didn’t have the time or resources to look at controls relating to voter registration, mail-in voting, ballot drop boxes, or the post-election auditing process. Practices in these areas would complement and back up the practices we reviewed.
- Further, elections are decentralized across Kansas’s 105 counties. Each county has different processes and controls, uses different vendors, etc. This decentralized system is an additional control for statewide election security. Impacting a statewide election would require defeating controls in multiple counties, each of which operates differently.
- Overall, the EAC best practices are a good goal to strive for. Having them all in place would certainly bolster counties’ election security. But it’s not realistic to expect counties to perfectly achieve them all. These controls take money and other resources to put in place, and counties have to balance election security costs against numerous other competing demands.
None of the 15 counties we reviewed had adequate written election security policies or guidance.
- No county we reviewed had comprehensive security policies or guidance. County officials said they relied on state law and a handbook the Secretary of State’s office provided. But this handbook simply provides the high-level guidance required to hold an election. It offers minimal information about county-specific election security practices.
- Many counties had at least a few standardized forms or checklists in place to help guide certain processes. But their quality and completeness varied across counties, and some counties had virtually nothing written down.
- We expected each county to have a comprehensive, regularly updated policy manual clearly outlining the county election officer’s expectations. Elections are complicated processes requiring many people, including county staff, election workers, and sometimes other county departments or contracted moving companies. Elections also happen infrequently, and county election officers described higher levels of turnover in recent years. Documenting required security practices is the first step to ensuring they happen.
Many things likely contributed to the issues we identified, including insufficient guidance and oversight at both the state and county levels.
- The state doesn’t appropriate funding to help counties pay for election security, and county election officers told us they don’t have enough time, staff, or money for every security practice we looked at. For example, Douglas County officials estimated they spend more than $1,000 each month on video cameras and alarms. Many counties, especially smaller counties, likely don’t have the resources for these types of security practices.
- The Secretary of State doesn’t proactively provide state-level guidance or make recommendations about minimum election security expectations. While they respond to counties’ questions, they told us they don’t do more because they don’t want to tell independently elected county clerks how to do their jobs.
- However, county clerks told us they would like greater state-level assistance with election administration. The Secretary of State’s office is in a unique position to offer county election officers meaningful support. They have both statewide influence and the requisite expertise to provide effective guidance and help counties of all sizes improve their practices.
- As noted in Part 1 of this report, the annual training the Secretary of State’s office provides county election officers is high level. It doesn’t get into topics like the importance of security controls or how to adequately design and practice them.
- Finally, county election officers may not be adequately training volunteer election workers or holding them accountable for following established practices.
- Election workers may not understand security controls’ importance or how to correctly carry them out. Counties with adequately designed practices sometimes had issues with election workers not following them. For instance, we saw many standardized forms across counties of all sizes that were filled out incorrectly or not at all.
- As we noted in Part 1 of this report, counties’ election worker training practices varied significantly in terms of their content and rigor. County election officers are responsible for designing and delivering these trainings. Some training materials we saw instructed workers to follow security controls. But they frequently focused instead on basic election processes, like setting up polling places or assisting voters.
- Finally, the strict time frames put on election processes likely makes it harder for county election officers to hold election workers accountable. County election officers said they feel under intense time pressure during elections. There simply may not be time or opportunity to correct security control problems during a live election. This makes training all the more important.
Conclusion
Election security has received much attention in recent years. In Kansas, the number of counties and decentralized structure of elections makes it difficult to know the statewide security status. This audit helps to provide at least a partial picture of Kansas’s election security. We reviewed counties’ policies and practices against a set of best practices for secure elections suggested by the federal elections agency. These controls are voluminous and have built in redundancies. Having them all in place would bolster counties’ election security. But it’s not realistic to expect counties of all sizes to have controls for all best practices because they take money and other resources to put in place.
As pointed out in both Part 1 and Part 2 of this audit, elections are extremely complicated with dozens of steps, sequences, and processes involved. We reviewed 15 Kansas counties across several election process areas. Because Kansas counties can operate elections differently and because they vary so much in size and population, the elections processes we reviewed looked very different from county to county.
Our results showed Kansas counties have many practices for ensuring the accuracy and security of elections, but they’re also missing or have weak practices in several important areas. That means security isn’t as good as it could or should be. While election officers took security seriously, our conclusions were based not on what they told us, but on what we could observe or verify in documentation. Larger counties generally had stronger security practices than smaller counties. The sheer volume of their people and equipment and complexity of their elections require larger counties to have more controls and better documentation to ensure things aren’t missed. Further, larger counties also have more financial and staff resources to dedicate to elections.
The results of our work provide an opportunity for counties, the Secretary of State’s office, and the Legislature to bolster Kansas’s processes. Elections are complicated processes and happen infrequently. A one-size-fits-all approach does not make sense for Kansas because the counties vary so widely in terms of size and complexity. However, these things make it even more important that there’s statewide guidance on baseline security expectations and training to support Kansas’s election security posture.
Recommendations
- The Secretary of State’s office should create example election security policies and standardized forms to offer to county election officers to use at their discretion. The Secretary of State’s office should consider working with officials from counties with stronger practices to adapt these practices for all counties to use.
- Agency Response: The Secretary of State’s office provides many standardized forms for conducting elections, many of which are posted on the Secretary of State’s website, which counties may use. The Secretary of State’s office has provided best practice white papers from a variety of federal security partners in the past few years. The office continually encourages counties to utilize the white papers to the greatest extent possible [allowing for resource availability]. Additionally, the office works one-on-one at the request of a county, to assist them in developing forms, policies, or processes. The office is willing to assist counties as needed as they develop security policies unique to their county. Every county is required to have on file a security policy and the Secretary of State’s office issues reminders to update that policy annually. Currently, a team of county election officers is developing more standardized forms and policies across all aspects of election administration which will be made available to counties to adopt as they see fit. This work started in April with the goal of providing forms and policies in early 2024.
- The Secretary of State’s office should use county election officers’ annual training or new certification program to train them in the importance, proper implementation, and effective oversight of election security statutes and best practices. This would include guidance on which security best practices counties should implement as a baseline.
- Agency Response: The Secretary of State’s office agrees with this recommendation and notes the following: The office provides security training on a periodic basis during annual training, which in prior years has included presentations from security officials from KSANG, DHS, CISA and private security specialists. In addition, the Secretary of State’s new certification training program, which is currently underway, includes security training as part of the base curriculum that is offered. The Secretary of State’s office also makes counties aware of security information and free training opportunities provided by CISA and DHS. This includes time-sensitive security information, as well as security reviews of network set-ups and on-site review of facilities.
- The Secretary of State’s office should provide guidance to county election officers on what materials to seal in ballot containers and what materials should not be sealed so they are available for public review.
- Agency Response: The Secretary of State’s office agrees with this recommendation and notes the following: Currently, the Secretary of State’s office provides reminders to county election officials both prior to and following each election concerning ballot security measures and ballot retention laws. The Secretary of State’s office will continue to provide reminders [and include emphasis on what should not be included in sealed ballot containers]. The agency notes this also will be covered in certification training and included in the election standards which are currently being updated and which are routinely used by county election officials.
Agency Response
On June 5, 2023 we provided the draft audit report to the Secretary of State’s office as well as Chase, Chautauqua, Dickinson, Douglas, Ford, Harvey, Jackson, Johnson, Lincoln, Miami, Riley, Russell, Sedgwick, Sheridan, and Wyandotte county officials.
The Secretary of State’s office’s response is below. Agency officials generally agreed with our findings and conclusions. We didn’t make recommendations to the counties, so their responses were optional. None chose to respond.
Secretary of State’s Office Response
The Secretary of State’s Office appreciates the LPA’s work in preparing the audit report reviewing Kansas’s policies and practices surrounding election security, and their understanding of the complexities, and the variances within the scope of state law, under which counties conduct elections. While the agency serves as a resource for county election officials (CEOs), ultimately, CEOs are independently elected officials who have discretion to conduct elections, within the scope of law and regulation, in a manner that best meets the unique needs of their county.
The audit reviewed certain best practices and state laws regarding election security in 13 Kansas counties. The audit recognizes, and the agency agrees, that many factors influence county election security practices, most notably, that the size and resources of a county are key drivers of practices across counties. CEOs are in the best position to assess the security within their county, and structure their election security practices accordingly. However, the Secretary of State’s Office agrees there are areas where election security policies and procedures may be strengthened, such as ensuring counties maintain an inventory of election results media, and is committed to proactively working with CEOs as detailed in the recommendation responses below.
Appendix A – Cited References
This appendix lists the major publications we relied on for this report.
- Election Management Guidelines. U.S. Election Assistance Commission.
- Policy on Direct Recording Electronic Voting Machines and Ballot Marking Devices (November, 2019). Verified Voting.
- State Requirements and the U.S. Election Assistance Commission Voting System Testing and Certification Program (September, 2020). U.S. Election Assistance Commission.
- Voting System Security and Reliability Risks (August, 2016). Brennan Center for Justice, New York University School of Law.
- Voting System Standards, Testing, and Certification (November, 2021). National Conference of State Legislatures.
- Voting Security Recommendations (August, 2020). National Institute of Standards and Technology, U.S. Department of Commerce.
Appendix B – Best Practices and State Laws
This appendix lists the best practices and state laws we reviewed for this report.
Overall Process Security
- Counties maintain inventory and tracking of voting machines, tabulation machines, and election results media.
- There is an inventory of equipment that appears to have been updated.
- The inventory of equipment includes quantities of equipment and electronic media.
- The inventory of equipment includes permanent and unique serial numbers of equipment and electronic media.
- The inventory of equipment includes tracking of equipment use (i.e., check-in and check-out documentation).
- The inventory of equipment includes tracking of repairs.
- Only trusted software is installed on voting and tabulation machines and election management computers.
- Software is EAC certified (i.e., meets voluntary voting system guidelines and was tested through a voting system test laboratory). (K.S.A. 25-4406 and 25-4613)
- Software is directly obtained from a trusted source (e.g., the vendor, an authorized contractor).
- All vendor modifications are required to be approved by the EAC.
- Paper ballots are available to confirm results.
- Elections use paper ballots (either hand marked or printed from a voting machine). (K.S.A. 25-4403 and 25-4406)
- Direct recording electronic voting machines should not be used.
Election Management Computer Security
- Election management computer activity is monitored.
- There is a well-defined procedure for monitoring each person with access to the election management computer.
- The election management computer access monitoring procedure includes access logs.
- The election management computer access monitoring procedure requires all work on the computer to be done in pairs (including by vendors, with election staff present).
- The election management computer cannot be used for other functions.
- Election management computer software is the only software installed on the computer.
- The election management computer is secured from unauthorized physical or virtual access.
- The election management computer is not connected to any networks. (K.S.A. 25-4403)
- The election management computer access monitoring procedure limits access (passwords only for election officials and access only for the functions officials are authorized to perform).
- The election management computer access monitoring procedure requires passwords to have length requirements.
- The election management computer access monitoring procedure requires passwords to have complexity requirements.
- Physical access to the area where the election management computer system is used is limited to authorized personnel.
- Authorized personnel with access to the election management computer system have unique codes for entry tracking.
- The area where the election management computer system is used is secured.
Ballot Security
- Control totals are used to account for all ballots and ensure the correct number is tabulated.
- Two-person integrity security measures are in place for recording daily ballot activity.
- Election officials verify that voting and tabulation machines are secured during election day through checks that the number of voters processed matches the number of votes recorded.
- End-of-day printed vote totals are accounted for using a two-person integrity security system.
- Election officials compare the number of ballots tallied with the number of voters for each voting site on a site-by-site basis. (K.S.A. 25-4412)
- Election officials comprehensively account for all ballots sent to polling places (i.e., voted, voted provisionally, spoiled, or unused).
- Controls are used to monitor the elimination of provisional ballots from tabulation.
- Rejected ballots are reviewed by at least two people to confirm the rejection.
- Officials document eligibility decisions for provisional ballots.
Voting and Tabulation Machine Security
- Voting and tabulation machines are checked to work properly and for physical damage when purchased.
- Every voting machine unit has undergone an acceptance test that includes running a mock election and ensuring the counts are correct.
- Every voting machine unit has undergone an acceptance test that includes verifying the machine’s physical integrity (e.g., no signs of physical damage; doors, locks, and hinges work well; hinge pins are not easily removed).
- Voting and tabulation machines are physically secured from unauthorized access while stored between elections.
- Physical access to the storage facility is limited to authorized personnel.
- Authorized personnel with access to the storage facility have unique codes for entry tracking.
- The storage facility is video monitored.
- Officials keep an updated key control list of all personnel with keys to the storage facility.
- Election office staff have passed a background check.
- Voting and tabulation machine accuracy is verified before elections.
- Logic and accuracy testing is performed by two or more people and documented.
- Tabulation machine accuracy is double-checked after elections. (K.S.A. 25-4411 and 25-4610)
- Public post-election tests are conducted on each tabulation machine.
- The public post-election tests process a pre-audited group of ballots for each candidate and each measure.
- The public post-election tests include one or more ballots for each office that have more votes than allowed by law, thereby testing for the equipment’s ability to reject overvotes.
Transfer and Movement Security
- Controls are used to monitor the deployment of voting machines, tabulation machines, ballots, and election results media to polling places.
- A record of election material transfer is kept for delivery of all supplies, including machines. (K.S.A. 25-2707)
- Controls are used to monitor the return of voting machines, tabulation machines, ballots, and election results media to the election office.
- A record of election material transfer is kept for the return of all supplies, including machines. (K.S.A. 25-2707)
- There is a chain of custody in place for ballots that ensures that ballots are in possession of two or more election officials of different parties at all times.
- Election results storage media are accounted for using a two-person integrity security system.
- End-of-day printed vote totals are transferred using a two-person integrity security system to the election office.
- Election results storage media are transferred using a two-person integrity security system to the election office.
- Voting and tabulation machine software is secured from tampering when deployed for elections.
- After logic and accuracy tests are completed, voting and tabulation machines are sealed with a tamperproof seal.
- Tamperproof seal numbers are documented on a transmittal sheet.
- Tamperproof seal numbers are checked against the transmittal sheet at each polling place by a two-person team.
- Voting and tabulation machines are secured and sealed with a tamperproof seal during transportation to the polling place.
- Opening zero proofs are printed for all tabulation machines.
- Voting and tabulation machines are physically secured from unauthorized access when deployed for elections.
- There is a key control list of all personnel with keys and access to facilities where voting and tabulation machines are present.
- Election officials verify that voting and tabulation machines are secured during election day through inspections for damage or tampering.
- Election results are secured from tampering during physical transfer to the election office.
- Official results are always computed by media that is physically transported from the polling place to the election office.
- End-of-day printed vote totals are transferred in numbered, sealed pouches to the election office.
- Election results storage media are transferred in numbered, sealed pouches to the election office.
Appendix C – Common Security Concerns
This appendix provides additional explanation about some election security concerns we heard that may be based on misunderstandings.
Nationally, electronic equipment certification testing under the most recent EAC guidelines is only just starting.
- We heard concerned citizens express concerns about voting and tabulation machines losing their EAC certification when the EAC releases updated standards. This certification depends on this equipment meeting the EAC’s voluntary voting system guidelines (VVSG). Machines are tested to meet these standards when they’re purchased and again when they receive a major software upgrade.
- The counties we reviewed were tested to VVSG 1.0, but that’s caused some confusion because those aren’t the most recent standards. The EAC adopted VVSG 1.0 in December 2005, VVSG 1.1 in March 2015, and VVSG 2.0 in February 2021. VVSG 1.0 and 1.1 created requirements and specifications intended to determine whether equipment meets basic functionality, accessibility, and security requirements. VVSG 2.0 goes further, describing how equipment should be designed and developed, as well as how it should operate. VVSG 2.0 reflects industry best practices and requires significant equipment upgrades.
- There is a delay between the EAC adopting the new standards and when voting systems can be tested to meet them. Nationally, two independent voting systems testing laboratories test all equipment to see whether they meet EAC standards. It takes time for them to switch to testing under new standards. The first of these 2 laboratories became capable of testing against VVSG 2.0 in November 2022, and the second became capable in December 2022. As of March 2023, just 1 voting machine system in the U.S. had been submitted for certification to VVSG 2.0.
- All equipment certified to past standards remains certified when the EAC releases new standards. Voting and tabulation machines are not decertified when the EAC releases new standards and are still valid and certified for use in elections. New standards only affect the testing process equipment must go through to obtain future certification. It doesn’t affect equipment certified to past standards.
Vote totals may go up and down or even return to zero on election night, but these are unofficial results that are never used in the final tabulation.
- We heard concerned citizens express concerns about unofficial election night results behaving erratically. For instance, vote totals sometimes going up and back down or even returning to zero.
- State law doesn’t require counties to report election night results. Secretary of State’s office and county election officials told us they do so as a courtesy to people anxious to hear the election results. On election night, a board of county election officials conducts an initial canvass to produce these results. They report the unofficial results to the Secretary of State’s office via phone, fax, or a secure online portal.
- During this unofficial canvass, the count may go up or down as the count progresses. It may even return to zero. County election officials told us these changes come from things like checking a possible discrepancy and starting over to ensure they’re providing an accurate unofficial count.
- The Secretary of State’s office told us unofficial results are never used in the official tabulation of election results. The unofficial election night results may differ from the official canvass conducted later. This is a separate process that typically begins the Monday after election day.
Several of the best practices we reviewed should prevent election fraud schemes like vote switching.
- We heard concerned citizens express concerns about fraud schemes based on voting and tabulation machines switching voters’ selections from one candidate to another. For instance, a voter selects candidate X on a voting machine, but the machine records a vote for candidate Y. Or a voter feeds a ballot with candidate X selected into a tabulation machine, but the machine records a vote for candidate Y.
- Several best practices and state laws we reviewed should help prevent vote switching schemes from succeeding.
- Counties should conduct acceptance tests on their voting and tabulation machines when they first receive them. This would ensure the machines are intact and functioning as expected. This includes correctly processing a test election, which would reveal whether votes are being recorded correctly.
- Before elections, counties should conduct logic and accuracy testing on their voting and tabulation machines. This would ensure the machines are still functioning as expected. This again includes correctly processing a test election.
- After elections, counties should conduct public post-election testing on all their tabulation machines. This would ensure the tabulation machines are still functioning as intended after the election. This includes correctly processing another test election.
- Finally, state law (K.S.A. 25-3009) requires counties to conduct post-election audits of a randomly selected 1% of all precincts. This manually compares the official tabulations of these precincts to the ballots. This would provide one final check to ensure the ballots were correctly counted. In 2022, Cherokee County officials caught a vendor programming error through this process. This is an example of a post-election control working. This is also an example of redundancy. This likely should have been caught sooner with other controls, but was caught nonetheless.
Appendix D – County Selection
This appendix lists the 15 counties we selected for review and the details we considered when making this selection such as their locations and populations. Population figures are 2020 estimates. As the appendix shows, the 15 counties we reviewed had a total population of 1.6 million (or 56%) of the 2.9 million total population in Kansas in 2020.
Chase County
- Voting machine vendor: Unisyn
- Voting machine type: Ballot marking device
- Total county population: 2,600
- Voting age population: 2,000 (77%)
Chautauqua County
- Voting machine vendor: ES&S
- Voting machine type: Ballot marking device
- Total county population: 3,300
- Voting age population: 2,600 (78%)
Dickinson County
- Voting machine vendor: ES&S
- Voting machine type: Ballot marking device
- Total county population: 18,600
- Voting age population: 14,100 (76%)
Douglas County
- Voting machine vendor: Unisyn
- Voting machine type: Ballot marking device
- Total county population: 121,300
- Voting age population: 94,100 (78%)
Ford County
- Voting machine vendor: Dominion
- Voting machine type: Ballot marking device
- Total county population: 33,700
- Voting age population: 17,900 (53%)
Harvey County
- Voting machine vendor: ClearBallot
- Voting machine type: Ballot marking device
- 2020 voting machine type: Direct recording electronic
- Total county population: 34,400
- Voting age population: 25,500 (74%)
Jackson County
- Voting machine vendor: Dominion
- Voting machine type: Ballot marking device
- Total county population: 13,200
- Voting age population: 9,900 (74%)
Johnson County
- Voting machine vendor: ES&S
- Voting machine type: Ballot marking device
- Total county population: 597,600
- Voting age population: 428,300 (72%)
Lincoln County
- Voting machine vendor: Unisyn
- Voting machine type: Ballot marking device
- 2020 voting machine type: Direct recording electronic
- Total county population: 3,000
- Voting age population: 2,300 (76%)
Miami County
- Voting machine vendor: ES&S
- Voting machine type: Hybrid ballot marking device/tabulator
- Total county population: 33,700
- Voting age population: 25,300 (74%)
Riley County
- Voting machine vendor: ES&S
- Voting machine type: Hybrid ballot marking device/tabulator
- Total county population: 74,100
- Voting age population: 58,600 (79%)
Russell County
- Voting machine vendor: Unisyn
- Voting machine type: Ballot marking device
- Total county population: 6,900
- Voting age population: 5,300 (77%)
Sedgwick County
- Voting machine vendor: ES&S
- Voting machine type: Ballot marking device
- Total county population: 515,400
- Voting age population: 360,800 (70%)
Sheridan County
- Voting machine vendor: Dominion
- Voting method: Hand-counted paper ballots
- Total county population: 2,500
- Voting age population: 1,900 (74%)
Wyandotte County
- Voting machine vendor: ES&S
- Voting machine type: Ballot marking device
- Total county population: 165,400
- Voting age population: 100,600 (61%)
